Networks and Protocols
Steven Zeil
Throughout this course, you will be learning to use with Linux computers to do useful tasks that programmers perform on a regular basis. But you don’t need to own a Linux machine for this course. You don’t even need to know where you can go to sit down at a Linux computer.
Instead, our focus will be on remote access over a network, allowing you to issue commands from your own PC to a Linux machine that you will likely never set eyes on.
1 Networks
This remote access will be made possible by a network, a collection of computers linked by communications paths and protocols. (A protocol is a step-by-step procedure for initiating, carrying out, and eventually terminating some kind of communication – more on that later.)
1.1 LANs, WANs, and the Internet
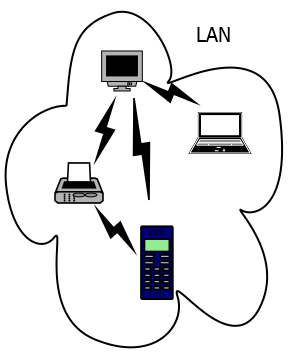
Most people connect their computers to a local area network (or LAN for short), using wireless or wired connections to communicate within a building or a cluster of nearby buildings.
When the connected machines are further apart, the network is called a Wide Area Network (or WAN for short). For example large corporations may create a WAN to connect their facilities in different cities.
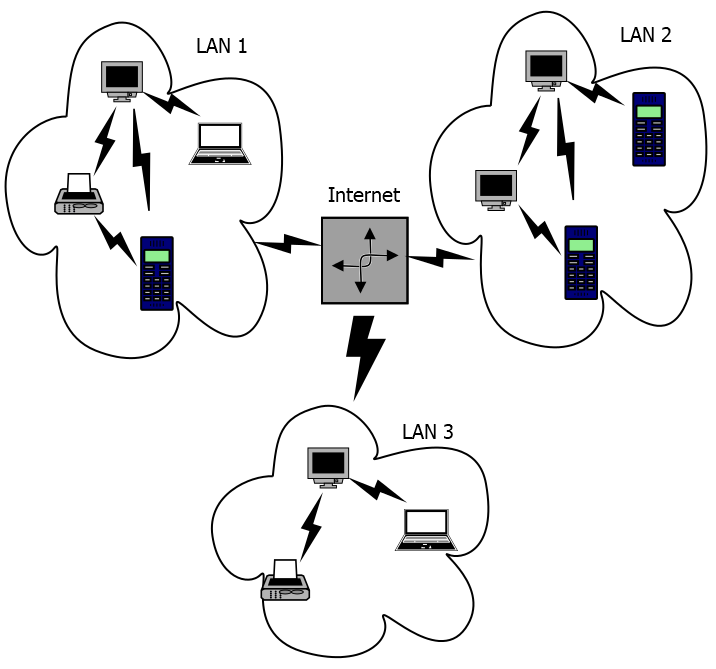
A very special case of a WAN is the Internet, a set of communications paths, protocols, and supporting devices that connects smaller LANs and WANs to communicate with one another.
2 Protocols
When you run into someone on the street or in a hallway that you want to have a conversation with, there are certain steps you go through.
- You greet them, or they greet you, with a “hello” or “hi” or “hey” or… The exact term doesn’t matter. It can be any of a number of socially accepted opening greetings.
- You await a reply of a similar greeting term.
- Optionally, you inquire after their health or emotional state.
- If you do so, you await a response.
- You begin to converse, speaking back and forth in turn, until…
- One of you says “good-bye”, or “so long”, or some other socially accepted phrase for signaling a desire to terminate the conversation.
- The other responds with a similar termination signal.
…and you each go on your way.
This is an example of a protocol, a set of mutually agreed-upon steps for initiating, carrying on, and terminating a communication.
Networks have many protocols, for different forms of communication. Some protocols, such as the ones that allow file sharing among Windows PCs or allow different PCs to share a printer, are confined within a LAN. Others, including the HTTP and HTTPS protocol for sending web pages, are designed to work across the Internet.
The Internet itself is defined by 3 major protocols:
-
The IP (Internet Protocol) protocol establishes the idea of an address on the Internet, e.g., 172.253.63.104.
-
The TCP (Transmission Control Protocol) protocol permits the sending of packets of information to an IP address.
Together, the TCP/IP protocols establish the communications pathways that carry the data for the other common protocols.
-
The DNS (Domain Name System) protocol allows IP addresses to be paired up with more descriptive names, e.g., as of this writing, 172.253.63.104 is one of the IP addresses known by the more common name www.google.com.
Computers on the Internet can be replaced because they have broken down or just need to be upgraded, and a machine with a new IP address may replace the old one, but if the DNS mapping is upgraded, the people using services provided by that machine will not notice the difference because the descriptive name has remained the same.
People using the Internet rarely concern themselves with the TCP/IP and DNS protocols. However, there are a whole host of other protocols running on top of those three that may provide services more familiar to you:
| Protocol | Transmits |
|---|---|
| HTTP | web pages |
| HTTPS | web pages (encrypted) |
| MPEG-DASH | streaming video |
| IMAP, POP | reading email |
| SMTP | sending email |
and some that we will be working with in this course:
| Protocol | Transmits |
|---|---|
| SSH | commands and responses |
| FTP | file transfer |
| SFTP | file transfer (encrypted) |
| X | graphic interfaces (windows, menus, buttons, etc), primarily within a LAN |
| X2Go | an accelerated version of X, optimized for the Internet |
3 Clients and Servers
A protocol defines a way to provide a service (e.g., viewing web pages, sending email).
In some protocols, such as the social greeting at the beginning of the previous section, either participant can take the initiative to begin communications, and the responsibilities and actions of both parties are pretty much equal or symmetric. That kind of protocol is called a peer to peer protocol.
Most protocols, however, define communication between a server, that provides a service to anyone who wants it, and a client, that requests this service. Clients and servers are programs that run with a network connection. The server sits quietly waiting to be contacted. When you want to make use of that service, you run a client that contacts the server, makes the request, and accepts the data from the server.
For example, you have probably heard the term “web server”, which is a program that can transmit web pages on request, using the HTTP or HTTPS protocol. A web browser, such as Chrome or Firefox, is actually an HTTP/HTTPS client. It knows how to make requests to a web server, how to process the data coming in via the HTTP or HTTPS protocols, and how to do something useful with that data (display it on your screen). The portion of a webpage URL between the “://” and the next “/” is the DNS name of the server that your client will connect to. So, if you were to view my home page at https://www.cs.odu.edu/~zeil/, your web browser would contact the server running on the machine whose IP address is known (to DNS) as www.cs.odu.edu.
Similarly, if you use a desktop email application such as Outlook, Thunderbird, or nearly any email app on your smartphone, you are running a program that combines one or both of the POP or IMAP clients for fetching email with an SMTP client for sending email. That part of your email address after the ‘@’ is actually identifying the servers that these clients will use, which is why that part of your address resembles the DNS names you are used to seeing in webpage URLs.
There’s a fair amount of smoke and mirrors that can hid the details of what clients and servers are involved.
-
We frequently use the terms “client ” and “server” to refer to the machines that are running the client and server programs. The machine known to the world as
www.cs.odu.edumay actually be running multiple web servers, and it might run servers for other protocols/services entirely. But if someone were to ask “what web server is that page from?”, we would probably reply “It’swww.cs.odu.edu” rather than “It’s Zeil’s copy of the Apache httpd server software running on the machinewww.cs.odu.edu.” -
Because the service defined by the combination of a web server, the HTTPS protocol, and a web browser is so flexible, it can show many things, including the output from a program running on the server machine. For example, when you use a web browser to get your ODU student email, you aren’t actually running email clients on your own PC. Instead, Google is running those clients, on your behalf, on its own machines, packaging up the results as a web page, and serving that web page to your web client (browser) via the conventional HTTPS protocol.
-
Many programs know how to launch other programs. For example, your email program may recognize a web URL within an email message and make it clickable. Now, your email client probably can’t handle the protocol to fetch that web page, and it may not have all of the code inside it to render web pages. But it may very well know how to launch the default web browser for your PC’s operating system, or it may have a setting that allows you to specify your preferred web browser to use in such cases.
Thus, when you click on the link, you email client may be able to launch a web browser to take care of that “foreign” protocol.
3.1 What Do You Need to Work on the Network?
You need to
- Know what protocol matches the task you want to accomplish.
- Run a client program that supports that protocol.
You can’t, as a general rule, mix and match clients and protocols. Don’t run a file transfer client if you want to view web web pages or read your email. Don’t run a web browser to transfer files to a remote machine. That’s like trying to dry your laundry in a refrigerator or storing food in your washing machine.
4 Virtual Private Networks (VPNs)
In many cases, organizations that provide a wide range of different network services are providing them within a Virtual Private Network (VPN).
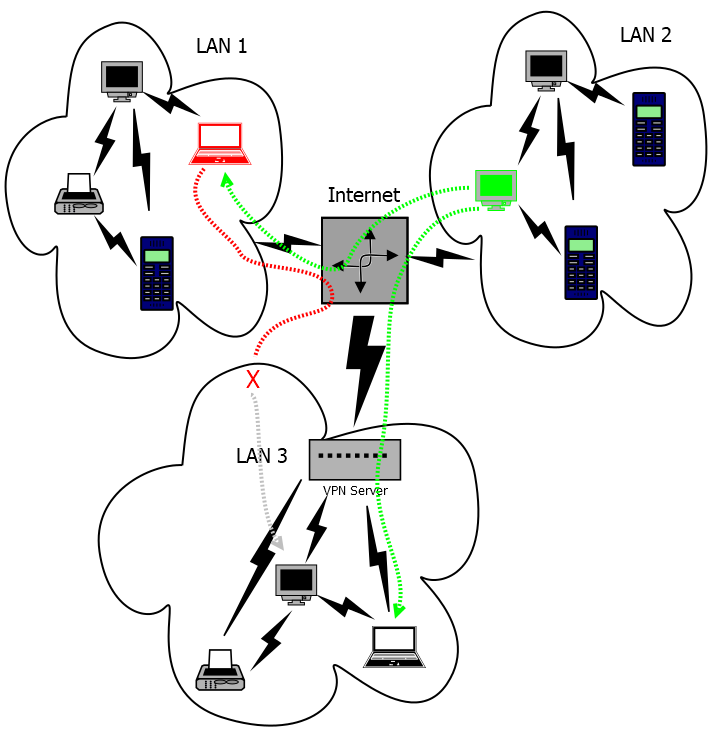
A VPN is a software construct that refines the boundaries of a LAN or WAN so that authorized machines can appear to be inside the LAN/WAN even though they are physically removed from it.
In the diagram to the right, the owners of LAN3 have decided to hide all or some of their servers behind a VPN.
If a machine that is not connected to the VPN (the red machine in the diagram) tries to access one of those protected servers, it will be blocked. More precisely, working through Internet, it can’t even see that those LAN3 servers exist.
But if a machine is authorized by the VPN server to access LAN3 (the green machine in the diagram)
- it can access servers within the protected LAN3
- and, to those servers, it appears to be itself within LAN3
- it can still access other internet servers outside of LAN3
- those servers still see it as existing at its “normal” position on the Internet
The ODU CS Department uses a VPN to protect most of its servers — pretty much everything except its web servers.
You will need to connect to the CS VPN for almost everything you do in this class except for browsing web pages.
It’s also worth noting that there are a number of commercial VPN services on the Internet that “protect” the entire Internet as if it were a single large LAN. Why do this?
- Remember that, if you use a VPN server to connect to a “protected” address, your connection appears to be coming from inside the VPN instead of from wherever you actually connect to the Internet.
- These VPNs provide, therefore, a way to anonymize your Internet usage, hiding your real IP address from the servers that you contact.
- The drawback to this anonymity, besides whatever charges you might need to pay to use these VPNs, is the slowdown that can result from routing all of your Internet traffic through the VPN server.

